SSL/TLS Configuration

SSL/TLSare cryptographic protocols that establish secure communication channels between web servers and browsers to protect data exchanged between them from unauthorized access and tampering
Introduction
SSL/TLSare cryptographic protocols that establish secure communication channels between web servers and browsers to protect data exchanged between them from unauthorized access and tampering. They ensure privacy and security over the internet, and are used in online transactions such as e-commerce and online banking.
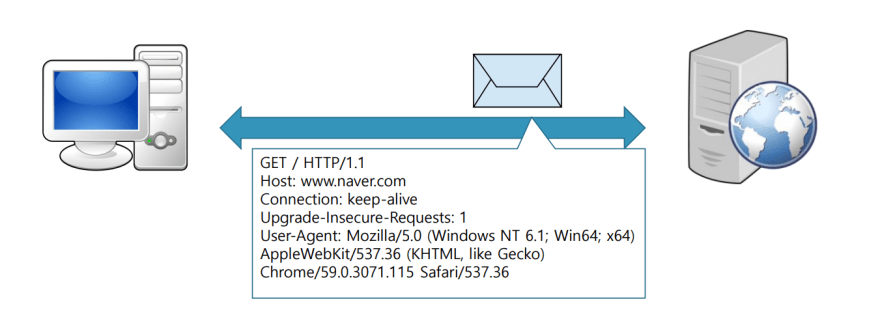
When a web browser connects to a secure website using SSL/TLS, the following process occurs:
- The browser requests a secure connection from the web server
- The web server responds by sending a digital certificate containing its public key to the browser
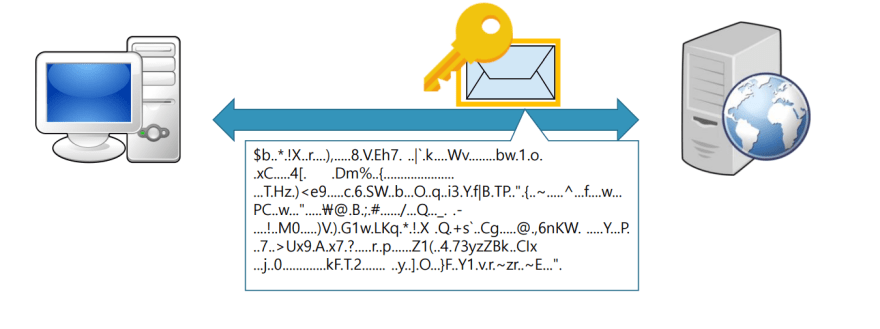
- The browser verifies the digital certificate and uses the public key to establish a secure session key
- The browser and server use the session key to encrypt and decrypt data exchanged between them
Applying SSL/TLS certificate
From the Apache web server
vi /etc/httpd/conf/httpd.conf
Right under theDocumentRootarea, we will add
127
128 Redirect "/" "https://"
129
We are redirecting theHTTPtraffic to theHttps
Installing ssl/tls
yum -y install mod_ssl
rpm -qa | grep mod_ssl
mod_ssl-2.4.6-98.el7.centos.6.x86_64
I will be creating my personal SSL certificate for this hands on as I won't be actually hosting this test website over the internet
Confirming if we haveopensslinstalled
rpm -qa | grep openssl
openssl-libs-1.0.2k-25.el7_9.x86_64
openssl-devel-1.0.2k-25.el7_9.x86_64
xmlsec1-openssl-1.2.20-7.el7_4.x86_64
openssl-1.0.2k-25.el7_9.x86_64
Creating the private key
openssl genrsa -out /etc/pki/tls/private/waji.key 2048
Generating RSA private key, 2048 bit long modulus
.....................................................+++
...............................+++
e is 65537 (0x10001)
Creating acsrfile for the key that we just created
openssl req -new -key /etc/pki/tls/private/waji.key -out /etc/pki/tls/private/waji.csr
This will ask for some information that will be related to the certificate
Now if we check,
ls -l /etc/pki/tls/private/
합계 12
-rw------- 1 root root 1675 2월 22 09:27 localhost.key
-rw-r--r-- 1 root root 1029 2월 22 09:32 waji.csr
-rw-r--r-- 1 root root 1675 2월 22 09:30 waji.key
We won't be creating a key or a csr file ourselves when we use an actual SSL/TLS certificate for our real website
Creating thecrtauthentication file
openssl x509 -req -days 365 -in /etc/pki/tls/private/waji.csr -signkey /etc/pki/tls/private/waji.key -out /etc/pki/tls/certs/waji.crt
Signature ok
subject=/C=KR/ST=Seoul/L=Gangnam/O=Waji/OU=Cloud/CN=waji/emailAddress=waji@test.com
Getting Private key
After this step we should have the.crtfile under/etc/pki/tls/certs
Entering the cert path in the config file
vi /etc/httpd/conf.d/ssl.conf
59 DocumentRoot "/apache/www"
75 SSLProtocol -ALL +TLSv1.2
80 SSLCipherSuite ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHERSA-AES128-SHA:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA384
100 SSLCertificateFile /etc/pki/tls/certs/waji.crt
107 SSLCertificateKeyFile /etc/pki/tls/private/waji.key
In the Apache Web Server configuration, we included all of the config files under/etc/httpd/conf.dmeaning this is also a part of the main configuration
Now, we need to test the configurations
apachectl configtest
Syntax OK
Restarting and checking the network status
systemctl restart httpd
netstat -antp | grep httpd
tcp6 0 0 :::443 :::* LISTEN 1457/httpd
tcp6 0 0 :::80 :::* LISTEN 1457/httpd
We are able to see 443 port and 80 port open for LISTEN
Setting up the firewall to accepthttps
firewall-cmd --permanent --add-service=https
success
firewall-cmd --reload
success
If we open our server from the browser
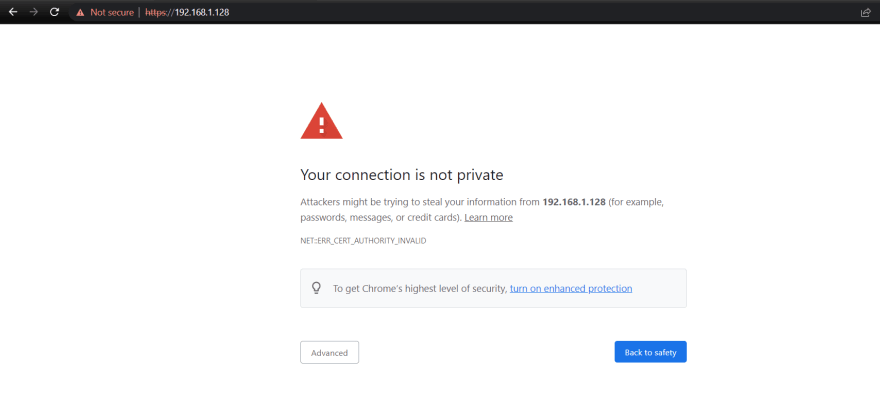
It shows unsafe because we aren't using a verified certificate from an authorized entity but we can confirm that it redirects tohttpsas we inteneded

